Blockchain technology has revolutionized various industries by providing a decentralized and secure method for recording transactions. Central to this security is the concept of a hash. But what exactly is a hash, and how does it help secure blockchain technology? This blog delves into the intricate role of hashing in blockchain, exploring its mechanisms, benefits and real-world applications.
What is a Hash?
A hash is a fixed-length string of characters generated from input data of any size using a hash function. The hash function processes the input data, known as the message, and produces a unique hash value. This value serves as a digital fingerprint of the data. No matter how large or small the original data is, the resulting hash is always of the same length.
Key Characteristics of Hash Functions
1. Deterministic
A hash function is deterministic, meaning that the same input will always produce the same output. This consistency is crucial for verifying data integrity in blockchain technology.
2. Fast Computation
Hash functions are designed to process data quickly, ensuring efficient performance even with large datasets. This speed is essential for the real-time processing of blockchain transactions.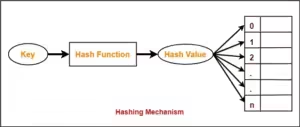
3. Preimage Resistance
Preimage resistance ensures that it is computationally infeasible to reverse-engineer the original input from its hash value. This property enhances data security by making it difficult to retrieve the original data from the hash.
4. Small Changes in Input Change the Hash Drastically
A slight alteration in the input data results in a significantly different hash value. This sensitivity ensures that any tampering with the data is easily detectable.
5. Collision Resistance
Collision resistance means that it is extremely unlikely for two different inputs to produce the same hash value. This property is vital for maintaining the uniqueness of each transaction in a blockchain.
How Hashing Secures Blockchain Technology
1. Data Integrity
Hashing ensures the integrity of data within the blockchain. Each block in the blockchain contains a hash of the previous block, linking them together in a secure chain. If any data in a block is altered, the hash will change, disrupting the chain and signaling tampering.
2. Block Creation and Mining
In blockchain networks like Bitcoin, miners compete to solve complex mathematical puzzles based on hash functions. This process, known as Proof of Work (PoW), involves finding a hash value that meets certain criteria. The first miner to solve the puzzle gets to add the new block to the blockchain and is rewarded with cryptocurrency. This mechanism not only secures the network but also incentivizes participation.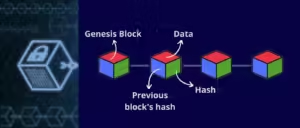
3. Digital Signatures and Authentication
Hashes are used in conjunction with digital signatures to authenticate transactions. When a user initiates a transaction, their private key signs the transaction’s hash, creating a digital signature. This signature is then verified by other network participants using the sender’s public key. This process ensures that the transaction is legitimate and has not been altered.
4. Efficient Data Verification
Because hashes are of a fixed length, they provide a compact representation of data, making it easier to verify large datasets. In blockchain, this efficiency is crucial for maintaining the performance and scalability of the network.
Real-World Applications of Hashing in Blockchain
1. Cryptocurrency Transactions
Cryptocurrencies like Bitcoin and Ethereum rely heavily on hashing to secure transactions. Each transaction is hashed and included in a block, which is then added to the blockchain. The integrity of each transaction is maintained through the hash links between blocks.
2. Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. Hash functions ensure the integrity and security of smart contracts by hashing the contract’s code and any associated data. This guarantees that the contract executes as intended without interference.
3. Supply Chain Management
In supply chain management, blockchain technology uses hashing to create a transparent and immutable record of goods’ movement. Each transaction or change of ownership is hashed and recorded on the blockchain, providing a secure and tamper-proof audit trail.
4. Voting Systems
Blockchain-based voting systems utilize hashing to secure votes and ensure the integrity of the electoral process. Each vote is hashed and recorded on the blockchain, making it nearly impossible to alter or tamper with the results.
Latest Developments in Hashing and Blockchain Security
1. Quantum-Resistant Hash Functions
With the advent of quantum computing, traditional hash functions may become vulnerable to attacks. Researchers are developing quantum-resistant hash functions to ensure blockchain security in the post-quantum era. These new algorithms are designed to withstand the computational power of quantum computers, maintaining the robustness of blockchain networks.
2. Advanced Cryptographic Techniques
New cryptographic techniques, such as zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge), are being integrated with blockchain technology. These techniques use sophisticated hashing methods to provide enhanced privacy and security. zk-SNARKs enable the verification of transactions without revealing any details about the transaction itself, preserving user privacy while maintaining data integrity.
3. Layer 2 Scaling Solutions
To address the scalability issues of blockchain networks, Layer 2 solutions like the Lightning Network and Plasma are being developed. These solutions use advanced hashing techniques to create off-chain channels for faster and more efficient transactions. By reducing the load on the main blockchain, these Layer 2 solutions enhance the overall performance and security of the network.
Future Prospects of Hashing in Blockchain
1. Enhanced Security Protocols
As blockchain technology evolves, new security protocols incorporating advanced hash functions will emerge. These protocols will provide even greater protection against threats, ensuring the continued integrity and trustworthiness of blockchain networks.
2. Interoperability Between Blockchains
Hash functions will play a crucial role in enabling interoperability between different blockchain networks. Cross-chain communication and asset transfers will rely on secure and efficient hashing methods to maintain data integrity and security across multiple platforms.
3. Integration with IoT
The integration of blockchain with the Internet of Things (IoT) will create new opportunities for secure and transparent data sharing. Hash functions will be essential for ensuring the integrity and security of data exchanged between IoT devices and blockchain networks.
Conclusion
The role of hashing in securing blockchain technology cannot be overstated. From ensuring data integrity to enabling efficient verification processes, hash functions are fundamental to the security and functionality of blockchain networks. As the technology continues to evolve, the development of advanced hash functions and cryptographic techniques will further enhance the security and scalability of blockchain applications. Understanding the significance of hashing is crucial for anyone looking to leverage the power of blockchain technology in today’s digital landscape.



