In today’s interconnected world, where digital communication and data exchange are omnipresent, ensuring the security of our networks is paramount. Whether you’re browsing the web, sending emails, or managing sensitive business data, understanding network security is crucial for safeguarding against cyber threats. In this comprehensive guide, we’ll delve into the essentials of network security, unraveling the mysteries behind terms like “network security key” and “firewalls,” and equipping you with the knowledge to protect your digital assets effectively.
Understanding Network Security:
Defining Network Security:
Network security refers to the measures put in place to protect computer networks from unauthorized access, misuse, modification, or denial of service. Essentially, it’s like setting up digital barriers and locks to keep your information safe from cyber threats. Imagine your computer network as a fortress, and network security is the defense system that guards it against intruders. It involves various techniques and technologies such as firewalls, encryption, and antivirus software to ensure that only authorized users can access the network and that data remains confidential and intact.
In simple terms, network security is about keeping your digital world secure and ensuring that your online activities are safe from hackers, malware, and other malicious entities. It’s like having a security guard for your computer network, constantly monitoring and protecting it from potential dangers. So, whether you’re browsing the web, sending emails, or sharing files, network security is essential for safeguarding your digital assets and maintaining peace of mind in the digital age.
Key Components of Network Security:
“Network security is like building a strong fortress around your digital world to keep it safe from cyber threats. Imagine your network as a house, and network security as the locks, alarms, and security guards that protect it. There are several important components to network security. First, there’s firewalls, which act as barriers between your network and the outside world, filtering out dangerous traffic.
Then, there are antivirus programs, which scan your devices for harmful software that could sneak in and cause damage. Encryption is another crucial component, like putting your messages in a secret code so that even if someone intercepts them, they can’t understand what’s being said. And don’t forget about authentication, which is like having a secret handshake to verify that someone is who they say they are before letting them in. By combining these key components, you can create a strong network security system that keeps your digital home safe from intruders.”
Importance of Network Security in the Digital Age:
In simple terms, network security is like a shield that keeps your online stuff safe. It’s all about making sure only the right people can access your information while keeping the bad guys out. Just like you lock your front door to protect your home, network security locks up your digital world to keep it safe from hackers and other online threats. It’s like having a guardian angel for your internet life, making sure you can browse, chat, and share without worrying about cyber trouble. So, next time you’re online, remember to thank network security for keeping your digital world safe.
Analyzing Security Keys for Networks:
What is a Network Security Key?
A network security key is like a digital password that keeps your Wi-Fi network safe. It’s a secret code that only you and your trusted devices know, allowing them to connect to your Wi-Fi network securely. Think of it as a special key that unlocks the door to your Wi-Fi world, keeping out unwanted visitors and ensuring that only authorized users can access your internet connection.
When you set up your Wi-Fi router, you create a network security key to protect your network from unauthorized access. This key acts as a barrier, preventing strangers or hackers from sneaking onto your network and potentially accessing your personal information or causing harm to your devices. So, whenever you want to connect a new device to your Wi-Fi network, you’ll need to enter this key to gain access. It’s an essential aspect of maintaining the security and privacy of your home or office network, ensuring that only those you trust can enjoy the benefits of your internet connection.
Types of Network Security Keys:
Certainly! When it comes to network security, understanding the different types of network security keys is crucial for safeguarding your digital assets. In essence, a network security key functions similarly to an electronic lock to prevent unwanted access to your Wi-Fi network. There are primarily two types of network security keys: WEP (Wired Equivalent Privacy) and WPA/WPA2 (Wi-Fi Protected Access). WEP keys are older and less secure, resembling a simple password that can be easily cracked by cyber attackers. On the other hand, WPA/WPA2 keys offer more robust encryption, making them significantly harder to breach.
Within the realm of WPA/WPA2, there are two variations: WPA and WPA2. WPA is an older protocol that has some vulnerabilities, while WPA2 is the current standard and is considered much more secure. In essence, opting for WPA/WPA2 ensures stronger protection for your Wi-Fi network, reducing the risk of unauthorized access and potential security breaches. It’s essential to choose a strong and unique network security key and regularly update it to bolster your network’s defenses against cyber threats. By understanding the different types of network security keys and their levels of security, you can take proactive measures to fortify your network and maintain a secure digital environment.
WPA3, short for Wi-Fi Protected Access 3, is the latest standard in wireless network security, designed to enhance privacy and protection for Wi-Fi users worldwide. It offers robust encryption techniques, making it harder for unauthorized users to access your network and intercept your data. With features like individualized data encryption and improved authentication protocols, WPA3 significantly strengthens security compared to its predecessor, WPA2. This new standard provides better defense against brute force attacks and enhances security for devices with limited computing power, such as IoT devices. WPA3 also introduces Simultaneous Authentication of Equals (SAE), a key exchange protocol that prevents offline dictionary attacks. Overall, WPA3 represents a significant advancement in Wi-Fi security, providing users with peace of mind knowing their wireless connections are better protected against potential threats.
How Network Security Keys Work?
Network security keys play a vital role in safeguarding our digital networks from unauthorized access. Consider them as virtual locks that control who can enter our digital domain. When you set up a wireless network at home or in your workplace, you’ll often come across terms like “network security key” or “password.” Essentially, these keys encrypt the data transmitted between your devices and the network, ensuring that only those with the correct key can decipher and access the information. It’s like having a secret code that allows you to unlock the door to your network while keeping intruders at bay.
Without the correct key, outsiders won’t be able to connect to your Wi-Fi network or intercept your data, adding an extra layer of protection against cyber threats. Whether it’s browsing the internet, streaming videos, or sharing files, having a strong network security key is crucial for maintaining the privacy and integrity of your digital communications. Remember, when it comes to network security, a strong key is your first line of defense against potential intruders. So, always choose a unique and complex key to keep your network safe from prying eyes and malicious actors. By understanding how network security keys work, you can take proactive steps to fortify your digital fortress and enjoy a safer online experience.
Importance of Securing Network Security Keys:
Securing network security keys is crucial for keeping your digital information safe from unauthorized access and cyber attacks. Network security keys act as the digital locks that protect your Wi-Fi network, ensuring that only authorized users can connect to it. Without proper security measures in place, hackers can intercept your network traffic, steal sensitive information, and even gain control of your devices. By safeguarding your network security keys, you prevent these potential threats and maintain the integrity of your digital environment.
Imagine your network security key as the key to your home. Just as you wouldn’t leave your front door unlocked, you shouldn’t leave your network vulnerable to intruders. With the increasing prevalence of wireless networks in homes and businesses, the importance of securing network security keys has never been higher. Hackers are constantly on the lookout for unprotected networks they can exploit, making it essential to take proactive measures to defend against such threats.
Securing your network security keys involves several key steps. First, ensure that you use a strong and unique password for your Wi-Fi network. Avoid using default or easily guessable passwords, as these can be easily cracked by hackers. Additionally, consider enabling encryption protocols such as WPA2 or WPA3, which provide an extra layer of security for your network traffic.
Regularly updating your network security keys is also essential for maintaining security. If you suspect that your network has been compromised or if you’ve shared your network password with someone you no longer trust, it’s crucial to change your network security key immediately. By staying vigilant and proactive in protecting your network security keys, you can minimize the risk of cyber attacks and ensure the safety of your digital assets.
Exploring Firewall Solutions:
Introduction to Network Firewalls:
Network firewalls are like digital security guards for your computer or device. They’re a special type of software or hardware that helps keep bad stuff out and lets good stuff in. Imagine your computer is a house, and the firewall is the gatekeeper. It checks all the things coming in and going out to make sure they’re safe. Firewalls use a set of rules to decide what’s allowed and what’s not. They can stop hackers, viruses, and other nasty things from getting into your computer and causing harm. Think of it as a protective barrier between your device and the wild world of the internet. Whether you’re browsing the web, sending emails, or downloading files, having a firewall is like having a strong lock on your digital door, keeping you safe from online threats.
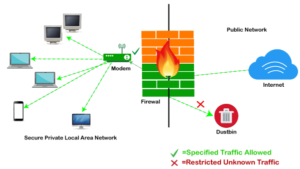
Types of Network Firewalls:
Stateful vs. Stateless:
Network firewalls are crucial components of cybersecurity, acting as barriers between your network and potential threats from the internet. When it comes to types of network firewalls, two main categories stand out: stateful and stateless firewalls. Let’s break down these concepts in easy-to-understand terms.
Stateful firewalls, often referred to as dynamic packet filtering firewalls, operate at the network layer of the OSI model. They keep track of the state of active connections passing through them. Imagine it like a vigilant guard at the gate of your network, carefully monitoring the incoming and outgoing traffic. These firewalls examine the context of each packet, checking if it’s part of an established connection or a new attempt to establish one. By maintaining a state table, they can make more informed decisions about whether to allow or block traffic based on predefined rules. This allows stateful firewalls to provide a higher level of security by analyzing the entire communication session, not just individual packets.
On the other hand, stateless firewalls, also known as static packet filtering firewalls, take a more straightforward approach. They evaluate each packet in isolation, without considering the context of the overall communication session. Picture it like a bouncer at a club checking IDs at the door – they decide whether to allow or deny entry based solely on the information presented to them at that moment. Stateless firewalls rely on predefined rules to filter traffic, typically examining packet headers for information such as source and destination IP addresses, ports, and protocols. While they are less resource-intensive compared to stateful firewalls, they may offer less comprehensive protection since they lack the ability to track the state of connections.
In summary, stateful firewalls offer more sophisticated protection by analyzing the context of network traffic, while stateless firewalls provide a simpler but less nuanced approach based solely on predefined rules. Both have their strengths and weaknesses, and the choice between them depends on the specific security needs and requirements of your network environment.
How Firewalls Enhance Network Security?
Firewalls play a crucial role in enhancing network security by acting as a digital barrier between your device and the internet. Consider it as a virtual bouncer, deciding which data packets can enter or leave your network. By analyzing incoming and outgoing traffic, firewalls can block unauthorized access attempts, prevent malicious software from infiltrating your system, and filter out harmful content. They also help enforce security policies, such as restricting access to certain websites or applications. Whether it’s a hardware firewall built into your router or a software firewall installed on your computer, these protective measures are essential for safeguarding sensitive data, protecting against cyberattacks, and ensuring a safe online experience. With firewalls in place, you can have peace of mind knowing that your network is fortified against potential threats.
Implementing Firewall Policies:
Implementing firewall policies is like setting up a security checkpoint for your digital network. Just as you’d decide who can enter a building and what items they can bring, firewall policies determine who and what can access your network and how they can interact with it. These policies act as rules or filters, governing the flow of data in and out of your network to prevent unauthorized access and protect against cyber threats. Think of them as the gatekeepers of your digital fortress, constantly monitoring incoming and outgoing traffic to ensure only legitimate connections are allowed while blocking suspicious or malicious activity. When configuring firewall policies, you have the flexibility to define specific criteria based on factors like IP addresses, port numbers, and types of traffic.
By strategically setting these rules, you can tailor your network’s defense mechanisms to suit your organization’s unique security needs. Whether you’re prioritizing certain applications, restricting access to sensitive data, or blocking known threats, firewall policies give you granular control over your network’s security posture. It’s like having a highly trained security team stationed at the entrance of your network, diligently screening every visitor to keep your digital assets safe from harm. So, by implementing effective firewall policies, you’re not just strengthening your network’s defenses – you’re building a robust barrier against cyber threats, ensuring the integrity, confidentiality, and availability of your data in today’s ever-evolving digital landscape.
Strengthening Computer and Network Security:
Best Practices for Computer Network Security:
Ensuring robust computer network security is essential in today’s digital landscape. Implementing best practices can help safeguard your systems and data from cyber threats. One crucial step is to use strong passwords and enable multi-factor authentication (MFA) to prevent unauthorized access. Regularly updating software and firmware patches is also vital, as it addresses known vulnerabilities that hackers could exploit. Encrypting sensitive data both in transit and at rest adds an extra layer of protection against interception and unauthorized viewing. Employing firewalls and intrusion detection systems (IDS) can help monitor and control network traffic, blocking malicious activity before it can cause harm. It’s also important to educate employees about security awareness, including recognizing phishing attempts and adhering to company policies on data handling. By following these best practices consistently, you can significantly reduce the risk of cyberattacks and keep your computer network secure.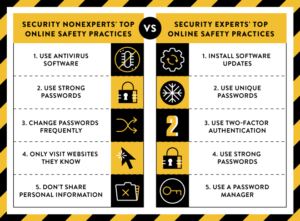
Importance of Regular Security Audits:
Regular security audits are like health check-ups for your digital systems. They help ensure that your online assets, such as websites, networks, and databases, are protected from cyber threats. By conducting these audits regularly, businesses can identify and fix vulnerabilities before they’re exploited by hackers. It’s essential to stay proactive in today’s cyber landscape, where cyber attacks are becoming more sophisticated and prevalent. Security audits also play a crucial role in compliance with industry regulations and standards, such as GDPR and PCI DSS. They provide assurance to stakeholders, customers, and partners that your organization takes security seriously. Plus, they can uncover inefficiencies and weaknesses in your security posture, allowing you to allocate resources effectively to address them. Ultimately, investing in regular security audits is an investment in the long-term resilience and success of your business in the digital age.
Effective Endpoint Security Measures:
Endpoint security is all about protecting the devices that connect to a network, like computers, laptops, and mobile devices. It’s crucial because these endpoints are often targeted by cybercriminals looking to steal data or disrupt operations. To ensure strong endpoint security, there are several key measures you can take. First, installing robust antivirus software helps detect and remove malware threats. Next, keeping software and operating systems up-to-date with the latest security patches is essential to patch known vulnerabilities.
Implementing strong password policies and using multi-factor authentication adds an extra layer of defense against unauthorized access. Additionally, encrypting sensitive data prevents it from being intercepted or accessed by unauthorized parties. Regularly backing up important files ensures you can recover them in case of a security breach or data loss incident. Finally, educating employees about cybersecurity best practices and the importance of being vigilant against phishing attacks helps create a security-aware culture within the organization. By implementing these effective endpoint security measures, you can significantly reduce the risk of cyber threats and protect your valuable digital assets.
Educating Employees on Cybersecurity Awareness:
Educating employees on cybersecurity awareness is crucial in today’s digital landscape, where cyber threats loom large. It’s essential to convey the importance of staying vigilant and proactive in safeguarding sensitive information. By providing simple yet effective training sessions, employees can grasp the fundamentals of cybersecurity without feeling overwhelmed. Topics such as recognizing phishing emails, creating strong passwords, and identifying suspicious links can empower them to become the first line of defense against cyber attacks.
Emphasizing the significance of regularly updating software and reporting any security incidents promptly fosters a culture of collective responsibility. Utilizing relatable examples and interactive exercises can make the learning process engaging and memorable. Encouraging open communication channels for reporting security concerns without fear of reprisal cultivates a culture of transparency and trust. Ultimately, by investing in cybersecurity awareness training, organizations equip their employees with the knowledge and skills needed to navigate the digital landscape securely, mitigating risks and fortifying their defense against cyber threats.
CONCLUSION:
keeping our networks safe is very important. We need to understand things like network security keys and firewalls to protect against bad things happening online. By following good rules and checking our security regularly, we can make our online world safer. It’s also important to teach everyone about being safe online. If we all work together and stay careful, we can keep our digital stuff safe.






Hello there, I found your site by way of Google even as searching for a similar topic, your website got here up, it seems to be good. I have bookmarked it in my google bookmarks.
Hi my family member! I wish to say that this post is amazing, great written and come with almost all important infos. I抎 like to peer more posts like this .
What i don’t realize is in truth how you are not really much more well-favored than you may be right now. You’re so intelligent. You recognize thus considerably in terms of this matter, produced me individually imagine it from numerous numerous angles. Its like men and women don’t seem to be involved until it抯 something to do with Girl gaga! Your individual stuffs outstanding. At all times care for it up!