Cybersecurity provides digital bodyguard protection for computers and their information. It might protect hackers from your computer and other activities on the internet. It can be put this way: It is a kind of digital key to your online door, ensuring that only trusted people can enter and keep out bad guys. It is mainly targeted to be protected from hacking in the digital area.
The extent of the cyber threat:
Cyber threats are like hidden digital problems that can be harmful to our computers. The concept of them is, in a way, like a big puzzle that hackers are trying to find the missing pieces with an eye toward breaking into computers and collecting information.
It consists of viruses, scams, and attacks that may, in general, be hazardous. Like locking your house from robbers, you are doing so to protect your computer.
These hackers can be kept out of our digital space only by having strong “locks” like passwords and antivirus tools. By being alert and taking smart online behavior, we can take care of the security in this digital world ourselves.
Malware:
The term Malware is the short form of malicious software, and, as the name goes, it acts like a digitally troublemaking gadget for your devices. Entered without permission into your devices, it damages them.
Types of malwares include viruses, worms, spyware. Think of them as tiny computer glitches that make everything go haywire. They can potentially slow down the speed of your computer device, collect your personal information, or even delete files.
Be safe by using antivirus programs, downloading carefully, and keeping software updated. It’s like having a shield for the digital world against all those invisible troublemakers.
Types of cyber threats:

Cyberterrorism
Cybercrime
Cyber-attack
Cyberterrorism:
Thus, cyberterrorism is considered as attacks through the Internet. These hackers exploit computers for ill-intended activities. They might sniff out information or cause damage to systems. From such threats, protection needs to be taken online.
Cybercrime:
The term defines illegal activities conducted through the Internet, grouping activities like scams and hacking. Technology is used by these criminals to either collect information or use it against others in harmful activities. Cybercrime requires that we be on the lookout and protect our personal information at all times.
Cyber-attack:
A cyber-attack is more like a backdoor attack on your computers, whereby the hacker is trying to break into your system and draws away or destroys information. It’s kind of like a robbery, and we protect ourselves with strong locks.
Types of Cyber Security:
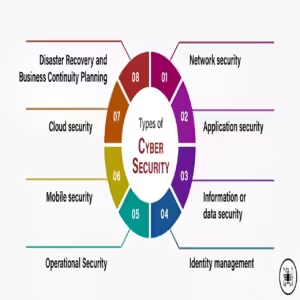
Application security
Cloud security
Critical infrastructure security
Data security
Endpoint security
Io T (Internet of Things) security
Mobile security
Network security
Operational security
Zero trust
Application security:
Application security works like a digital security guard for your computer programs. Imagine your apps are houses; app security would act as the lock at the front door and the alarm system inside that protects the apps from hackers who might want to break into your computer to collect information.
The developers use special tools and a lot of rules to build strong defenses and ensure only the right people can gain access to the app. The best way to describe it would be securely providing a space for your apps to live, with no unwanted visitors.
Quite simply, application security tames the digital world.
Cloud security:
Think of cloud security as more like a digital guardian for your online data. Storing data in the cloud is almost equivalent to putting it in an online safety box. Cyberattacks must be prevented on that “safety box”.
Cloud security involves special tools and measures taken to ensure the integrity and safety of your data against hackers and other dangers. It would be something like securing digital belongings with a lock and key, passwords, and some security guards guarding them.
So be it, your pictures, documents, or any such digital thing, cloud security ensures it stays safe.
Critical infrastructure security:
Critical Infrastructure Security: Protecting all the important things that keeps our society running in a bumper flow. Take care that the power, transport systems, and communication infrastructures are secure from hacking or any other threats. It’s like protecting the important things that keeps our society running.
It’s about making sure things like power plants, transport systems, and communication networks are safe from hackers or other threats. Imagine such a shield protecting those things which we need every day to live comfortably.
This security comes with smart technology and plans to fight off any disruption so that we can be free to carry on with our day-to-day running activities without these key services faltering.
Data security:

It’s like a virtual shield, securing our information against hackers or any other threats. This is comparable to protecting data through the use of passwords, antivirus software, and encryption—exactly what we do to lock up our houses.
This spans from emails, photos, to even bank details. In a world where we share so much online, data security only allows accredited access to our information for use, thus averting the threat of cyber-attacks on our privacy.
It’s a digital guardian that protects our online activity and puts everybody at peace while we navigate in this very vast internet.
Endpoint Security:
Endpoint security works like a digital security guard for your devices. Consider your computer, tablet, or phone—a castle in which every entry point is an opening through which cyber threats could enter.
Endpoint security does this by defending these many entry points, such as USB ports or software, at the doors and windows to your fortress, against the very insidious trespassers known as viruses and malware breaking in. It screens and blocks suspicious activity—a shield that holds your digital castle safe from infiltration.
This way, you’ll be able to surf the internet, download files, and use your gadgets as much as you want without fear of unseen dangers. In this way, endpoint security works as the digital protector of your devices, saving them from unknown threats lurking in the cyber world.
Io T (Internet of Things) security:
The security on Io T is akin to putting a digital lock on our smart devices to protect them. Imagine every single thing in your house being vocal: lights, refrigerators, even the collar of your pet.
The digital world brings all of them together, interconnecting life into one place for ease. Just as much as we lock the doors to our houses, so we must lock up our digital ties.
IoT security ensures smart gadgets only listen to correct orders and avoid unwanted activity. It’s like a guard for all of your digital things, making sure that your smart world is safe and secure. It’s a kind of cyber security.
Mobile Security:

Mobile security acts as a shield to your phone, keeping it safe from hacker or online threats. It’s much like a robust wall around your personal information, photos, and apps.
Making a robust password is much like fitting a robust lock to your electronic gateway. Downloads of software can be done only from trusted sources to avoid threats.
Updating is a crucial part of phone activity, as it is necessary to fight against threatening software, which evolves over time. By implementing the above steps, you can make your mobile a completely safe and secure platform for storing your precious data.
Network security:
Network securities are like digital armor over your online activities. Imagine it to be like a fortress that protects your information. This is securing any computer system and a network from an unauthorized access and cyber-attack.
This includes passwords, encryption keys, antivirus measures taken for safeguarding data. Network security is very important because it blocks hackers from collecting sensitive or, at times, personal information.
It means that by updating and keeping guard over your defenses regularly, you are ensuring a safe and secure online experience, just like having a reliable guardian for your digital world.
Operational security:
OPSEC, Operational security. OPSEC is like some sort of secret plan concerning the keeping of important information safe. You can think about it as if you have some sort of very special treasure and you really want to be sure that nobody finds out where it is kept. OPSEC, in a similar way, equates to keeping secrets and keeping things to oneself.
It could refer to anything from passwords to personal details and sensitive plans. Via carefulness of what we share and how we share it, we can make sure that our information remains safe in the vault, not paraded in the open air, and doesn’t find its way into the wrong hands.
In OPSEC, we shall be concerned with guarding our secrets like a treasure hidden in a secret place.
Zero trust:

Zero Trust is a cyber security concept which essentially says that no entity should be trusted with a network, even when already inside. The approach challenges the traditional model of security by assuming that threats can arise from both within and outside.
Zero Trust means verifying and validating every single entity—which may try to connect to a network from inside or outside. This approach encourages constant monitoring and strict access control, hence reducing the possibilities of a data breach.
A Zero Trust model elevates an organization’s general security stance, hence making the hackers’ job hard to exploit weaknesses and provides a digital environment that is safe. This is some form of cyber security.
Conclusion:
Cyber security works like a shield to our online world from different threats. Think of this as a team of vigilant guards for our devices, data, and digital spaces. It is truly the case that each part of cybersecurity is important.
This includes fighting off malware troublemakers and securing against cyber threats, such as terrorism and crime.
Each one—from the watchful ones of application security to the protective nature of cloud security and the very careful guard of endpoint security—brings about a safely secured and reliable digital environment.






Thank you for writing this article. I appreciate the subject too.
Thank you for your post. I really enjoyed reading it, especially because it addressed my issue. It helped me a lot and I hope it will also help others.
Please tell me more about this. May I ask you a question?
sure.
I’d like to find out more? I’d love to find out more details.